Everything You Need to Know About Assist RAG
 Rajesh
Rajesh- 0
RAG’s advanced system Assist functions as an AI-based technique that controls information searches and improves the correctness of obtained responses. The system goes beyond conventional RAG tools by integrating routine aid services together with moral validation algorithms and knowledge adaptation methods to conduct effective real-time informed responses.

The following guide demonstrates how Assist RAG performs and shows its applications together with its advantages and limitations while it also presents a Python-based implementation plan.
1. How Does Assist RAG Work?
The standard RAG system receives improvement through Assist RAG by adding three essential features.
a. Enhanced Retrieval Mechanism
The real-time knowledge augmentation with multi-source validation enables Assist RAG to generate more precise retrieval results.
Key Innovations:
- The system implements multi-source retrieval as a method to gather reliable data from both structured and unstructured sources.
- Dynamic relevance filtering establishes a system that displays the most completely relevant answers which reduces erroneous content.
- The system obtains real-time adaptive knowledge ingestion that operates dynamically to accept and manage brand-new data for ensuring current responses.
b. Context-Aware Generation with Ethical Guardrails
The response generation capability in Assist RAG follows ethical AI principles which guarantee fairness and accurate results while preventing bias in decision making.
Key Innovations:
- Bias detection algorithms together with corrective mechanisms identify and eliminate misinformation and stop undesirable unethical responses.
- The system stores memories in a way that ensures private materials stay protected from improper uses.
- Contextual summarization produces short yet accurate summaries based on retrieved information to deliver clear responses.
c. Self-Improving Learning Loop
Assist RAG includes self-learning mechanisms that make it smarter throughout its operational period.
Key Innovations:
- The adjustment of response generation occurs due to reinforcement learning when feedback and performance metrics are received.
- The AI hallucination detection system helps to stop the production of unreliable and incorrect automated responses.
- The security system autonomously adjusts the filtering mechanisms to stop unauthorized accesses or infiltration.
2. Why and When to Use Assist RAG?
Running Assist RAG will benefit your tasks when you need quick and exact data retrieval combined with accurate content creation. The system proves useful for various fields of application.
Customer Support & Virtual Assistants
- The tool increases chatbot performance through its capability to deliver contextually specific and tailored responses.
- The system enables interactions beyond scripted sequences therefore improving user-environment dialogue.
Healthcare & Medical Research
- Medical data retrieval becomes feasible with the help of doctors and researchers through this system.
- The framework enables organizations to maintain compliance with HIPAA along with GDPR because it blocks protected sensitive healthcare information from being accessed.
Financial Analysis & Risk Management
- Real-time financial insights are possible through the system which always preserves privacy.
- The system detects bizarre database requests that seem criminal in nature.
Legal & Compliance Monitoring
- The system enables users to obtain both case law material and compliance standards.
- Query monitoring allows the system to protect intellectual property from theft.
Cybersecurity & Threat Intelligence
- Through its capabilities you can track and nullify false information and stop phishing attempts from happening.
- AI security protection gets enhanced by an unauthorized data request filtering system.
3. Pros and Cons of Assist RAG
Pros:
1. Enhanced Accuracy :
- Multi-source retrieval increases response reliability.
- AI-driven contextual filters reduce misinformation.
2. Data Security & Compliance :
- Adheres to GDPR, HIPAA, and industry-specific compliance standards.
- The system employs secure memory approaches to stop unauthorized access of data.
3. Improved User Experience:
- Through the adaptive learning feature the system enhances user response effectiveness as users interact with it more often.
- The system provides concise meaningful summaries by understanding the context of user requests.
4. Efficient Resource Utilization:
- The search and retrieval system operates at peak efficiency to decrease machine runtime requirements.
- Advanced indexing improves system performance.
Cons:
1. High Initial Implementation Cost:
- Implementing the system demands major capital expenditures for the training of AI models and their subsequent deployment.
2. Latency in High-Security Environments:
- The generation of responses becomes delayed slightly when security checks need to be performed.
3. Integration Challenges:
- Because existing enterprise systems need an integration customization process for this approach.
4. Risk of False Positives:
- The application of very strict security limits has the potential to prevent legitimate system queries from passing through.
4. Python Implementation of Assist RAG Using Secure Retrieval
Assist RAG secured document retrieval with context-based response generation operates through this following Python code example.
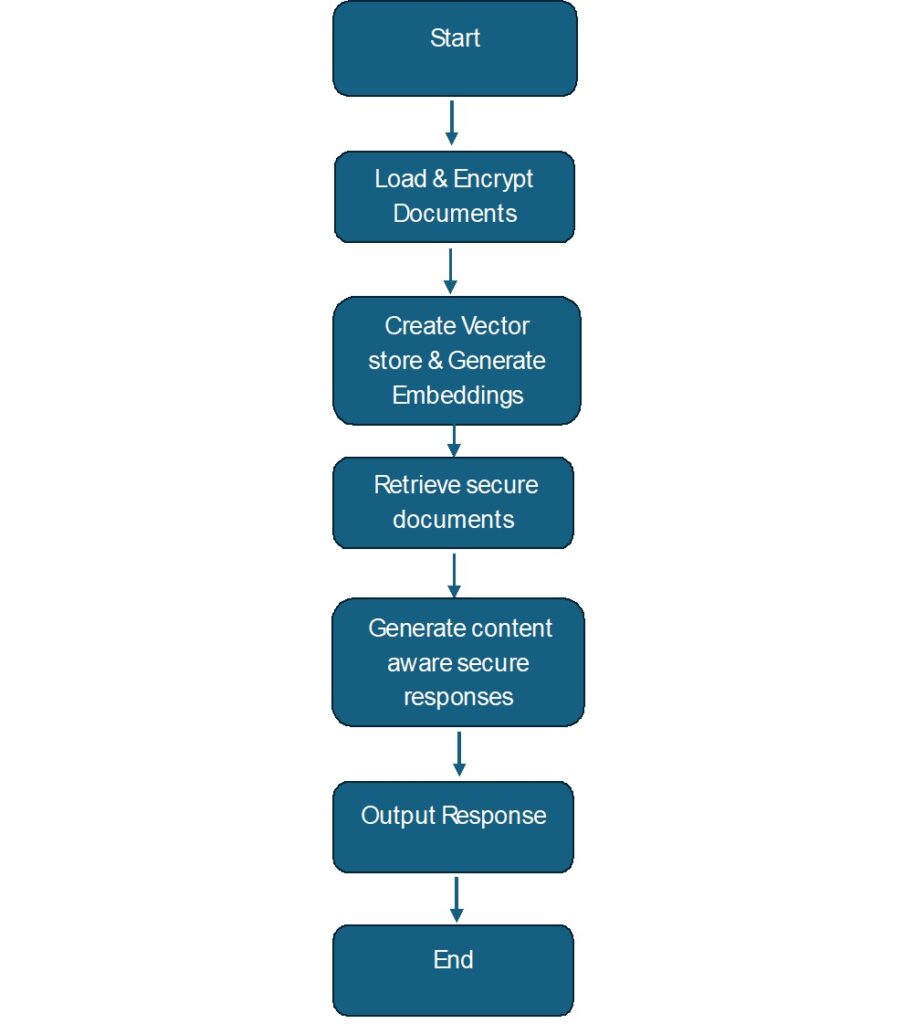
Step 1: Install Dependencies
The required Python libraries to install are langchain plus faiss-cpu together with cryptography and pypdf and transformers.
Step 2: Load and Encrypt Documents
from langchain.document_loaders import PyPDFLoader from langchain.vectorstores import FAISS from langchain.embeddings import HuggingFaceEmbeddings from cryptography.fernet import Fernet import os # Generate encryption key key = Fernet.generate_key() cipher_suite = Fernet(key) Next proceed to load PDF files while encrypting them with the PDF files renamed to secure_data.pdf. pdf_path = "secure_data.pdf" loader = PyPDFLoader(pdf_path) documents = loader.load() encrypted_docs = [cipher_suite.encrypt(doc.page_content.encode()) for doc in documents]
Step 3: Implement Secure Retrieval
embedding_model = HuggingFaceEmbeddings()
vector_store = FAISS.from_documents(documents, embedding_model)
def retrieve_secure_documents(query, k=3):
results = vector_store.similarity_search(query, k=k)
return [cipher_suite.decrypt(result.page_content).decode() for result in results]
Step 4: Generate Context-Aware Secure Responses
from transformers import AutoTokenizer, AutoModelForSeq2SeqLM
tokenizer = AutoTokenizer.from_pretrained("facebook/bart-large-cnn")
model = AutoModelForSeq2SeqLM.from_pretrained("facebook/bart-large-cnn")
def generate_secure_response(query):
context = retrieve_secure_documents(query)
input_text = query + "\n" + "\n".join(context)
inputs = tokenizer.encode(input_text, return_tensors="pt", max_length=512, truncation=True)
outputs = model.generate(inputs, max_length=50, num_beams=5, early_stopping=True)
return tokenizer.decode(outputs[0], skip_special_tokens=True)
# Example usage
The question asks how artificial intelligence affects cybersecurity.
response = generate_secure_response(query)
print("Generated Secure Response:", response)
Conclusion
Assist RAG marks an important development in AI technology for information search and response creation. This system leverages three core features which guarantee the generation of secure responses at high levels of contextual awareness through an AI system.
Future Enhancements:
- Users can utilize the Assist RAG system through edge computing deployments to execute the program on low-power devices without losing operational speed.
- The system incorporates decentralized AI learning through Federated Learning to attain better security and operational efficiency.
- Multi-Modal Retrieval: Extending retrieval capabilities to images, audio, and video data.
- The powerful abilities of Assist RAG will transform AI applications in various fields by establishing secure systems that precisely retrieve knowledge while generating responses effectively.
Author
-

Rajesh Yerremshetty is an IIT Roorkee MBA graduate with 10 years of experience in Data Analytics and AI. He has worked with leading organizations, including CarDekho.com, Vansun Media Tech Pvt. Ltd., and STRIKIN.com, driving innovative solutions and business growth through data-driven insights.
View all posts
